WHAT TRIDIUM IS DOING—DESIGNING SECURITY FOR OUR PRODUCTS
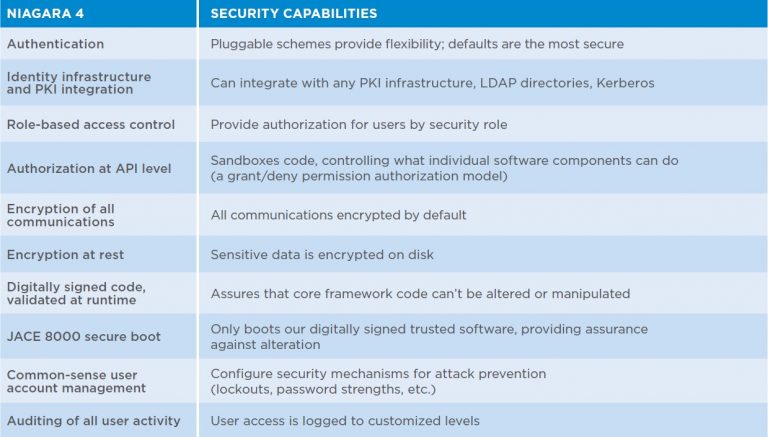
With people, processes and technology in mind, we at Tridium have developed an approach to cybersecurity that can be customized to the security policy of any organization. Our approach for doing this revolves around making it easier for our customers to secure our software, along with enforcing good “cyber behavior” through technology controls.

OUR “SECURE BY DEFAULT” PRINCIPLE
Make security easier: default to
the most secure configurations
• All transmissions encrypted
• Users forced to have strong
password strengths
• Users set up with the strongest
authentication mechanism
• User lockouts upon consecutive
bad logins
Do the right thing, regardless
of configuration
• Encrypt sensitive information at rest
• Digitally signed code: validated at
runtime
• JACE® 8000 secure boot: trusted
software validation at boot-time
Force administrators to do the
right thing
• Factory default password must be
changed after commissioning
Provide stronger configuration
options based on the best practices
• Articles, documentation and
TridiumTalks provide detailed
guidance
BEST PRACTICES, BASED ON LESSONS LEARNED
- Don’t expose your devices on the internet
- Use a defense-in-depth network security strategy
- Change “factory default” credentials
- Patch your systems
- Protect yourself from ransomware attacks
- Always use encrypted communications
- Always follow documented best practices for securing your devices and systems
- Don’t forget physical security
- Undergo formal threat and risk assessments
- Don’t forget about “people, processes and technology”
